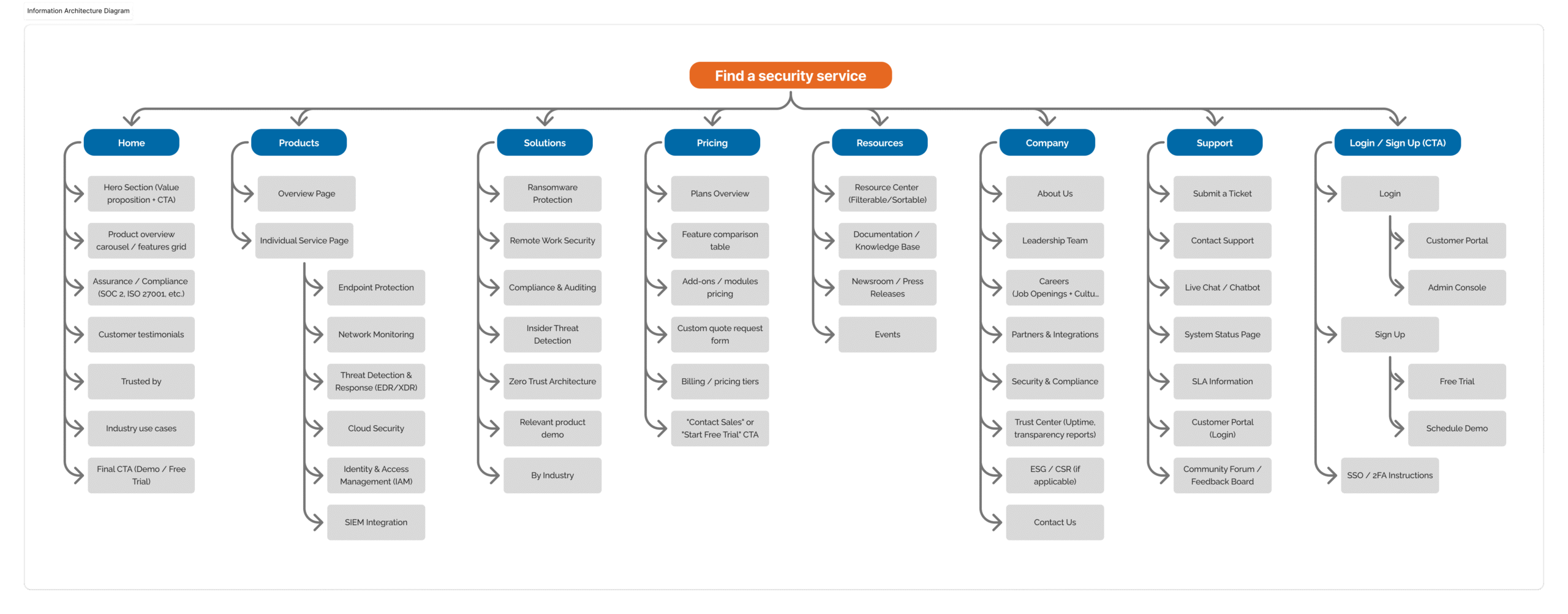
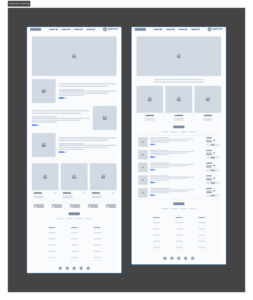
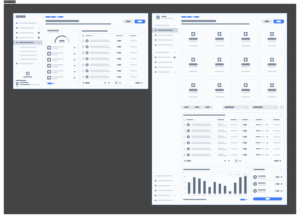
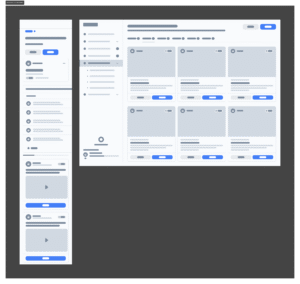
The outcome
Defendify became known as one of the first platforms to unify people, process, and tools for cybersecurity, not just for IT experts, but for everyday businesses. The design approach helped differentiate it in a crowded, technical market, garnering multiple awards since launch.
The case study
Defendify
Powering providers, protecting businesses.

Project summary
The product
Defendify is a cybersecurity solution that protects businesses from online threats. It caters to small and midsize companies and organizations without security teams, including IT and technology providers across all industries.
Defendify offers an integrated suite of cybersecurity tools for prevention, detection, and response.
Client
Role
UX/UI Principal Designer
Market Researcher
UX Researcher
Responsibilities
- User research
- Competitive audits
- Ideation workshops
- User flows & info architecture
- Low fidelity wireframing
- Prototyping
- High fidelity UI mockups
- Critique presentations
- Usability testing
- Design systems
- Accessibility
- Brand identity
- Foundational visual elements
The mission
To make cybersecurity possible for all organizations, regardless of size, by providing a comprehensive, easy-to-use platform that continuously improves security posture without requiring deep technical expertise.
P R O J E C T S U M M A R Y
The problem
The main challenge lies in the fact that the process begins with a set of services delivered within a brief timeframe, followed by services that are provided both intermittently and continuously.
Additionally, the initial services that are performed over a short period of time are not a one-time service. While these services will be the first set of services done when starting a new program, said services will occur at the beginning of each year (the nature of the work will be slightly different, but the same services are required to start each year).
User Sentiment
P R O J E C T S U M M A R Y
The solution
Defendify provides each of its customers with a running program of cybersecurity that includes three key layers of security: Foundation, Culture, and Technology. A “program” can be characterized as follows:
User Needs
P R O J E C T S U M M A R Y
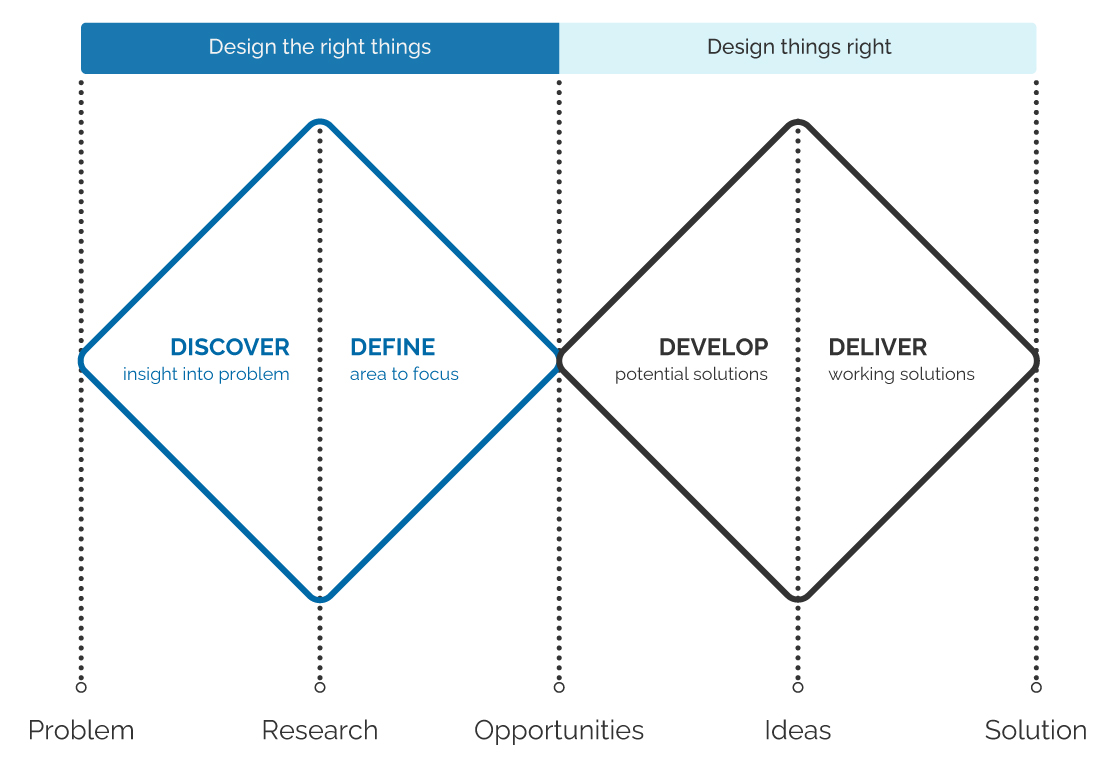
Design process
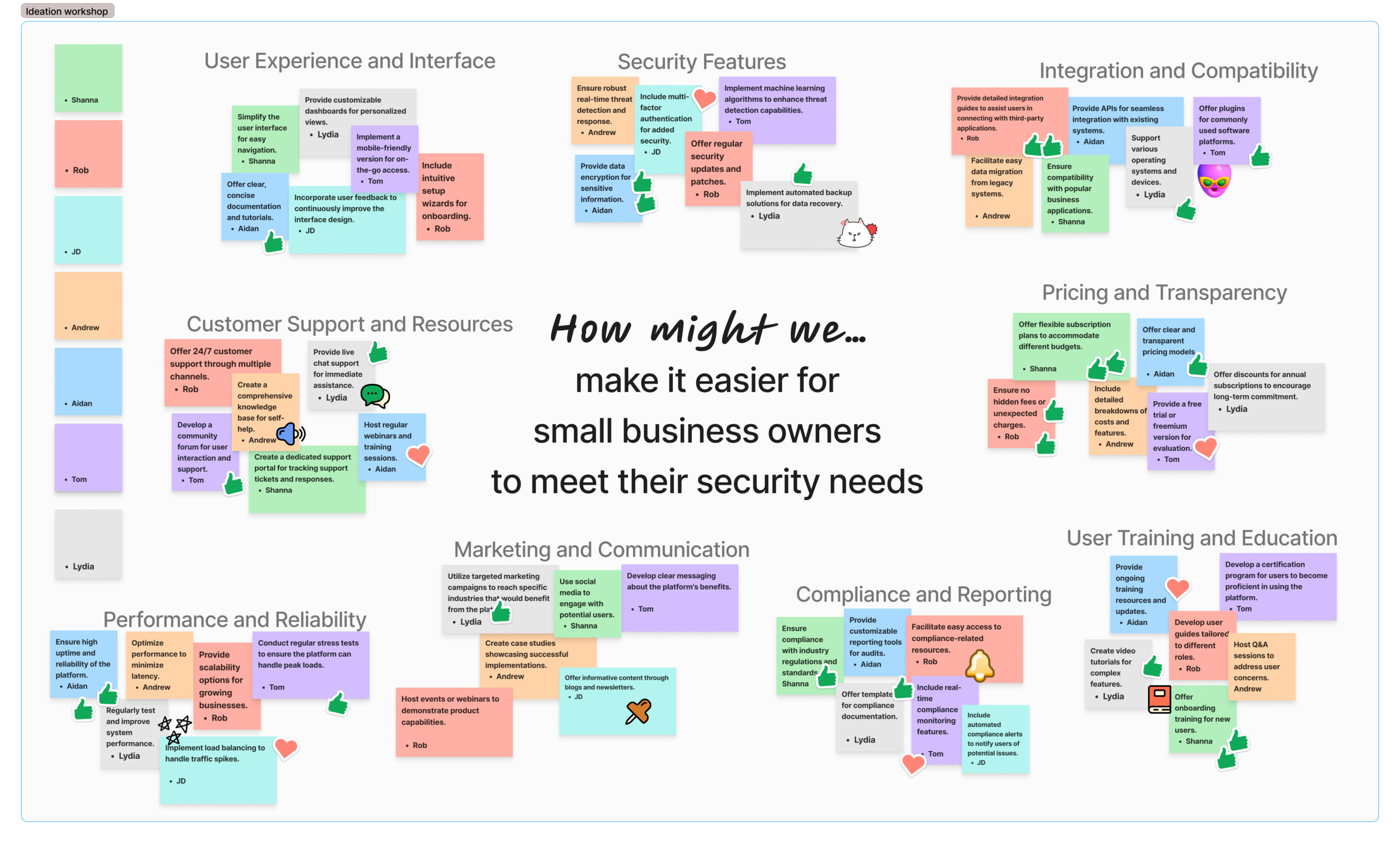
Being the principal designer I approached this design challenge using two distinct types of thinking:
- Divergent: I kept an open mind to explore a wide range of ideas.
- Convergent: I then collaborated to narrow down our options and identify the best solution.
User insight
U S E R I N S I G H T
User interviews
I carried out preliminary research with Defendify base users to gain deeper insights into their needs and challenges within the current flow.
Research type
Location
- US North-East small business
- remote
Participants (7)
- 2 IT Manager/Director
- 1 IT Support Specialist
- 3 Business Owner/Entrepreneur
- 1 Network Administrator
Participants
- ~45 minutes session
U S E R I N S I G H T
Competitive Landscape
Defendify’s core differentiation lies in comprehensive integration across Culture, Foundation, and Technology. In a fragmented cybersecurity market filled with point solutions, Defendify offers a unified, user-friendly platform designed for businesses without large IT teams. This positions it well for SMBs seeking broad protection without complexity, setting it apart from competitors who are often narrowly focused.
🔹 Culture (Human Behavior + Awareness Training)
These companies focus on security awareness training, phishing simulations, and behavior change:
-
KnowBe4
-
Cofense
-
NINJIO
-
Gophish
Defendify competes by embedding culture-focused tools into its platform, positioning itself as an alternative to pure-play awareness vendors.
🔹 Foundation (Risk Management + Compliance Frameworks)
This segment includes organizations that emphasize policies, governance, training, and risk assessment:
-
Survive Cyber
-
CRONUS
-
SANS Institute
-
Center for Internet Security (CIS)
-
Coalition
-
Corvus
Defendify overlaps by offering foundational modules like risk assessments, policy templates, and compliance guidance, which competitors often deliver as standalone services.
🔹 Technology (Security Tools + Threat Protection)
These companies specialize in endpoint protection, threat intelligence, vulnerability scanning, and password management:
-
Dark Cubed
-
LastPass
-
Tenable
-
SpyCloud
-
Fortinet
-
Norton by Symantec
Defendify differentiates itself by incorporating select technological tools (e.g., vulnerability scanning, device monitoring) into a broader platform, without requiring IT or deep security expertise.
U S E R I N S I G H T
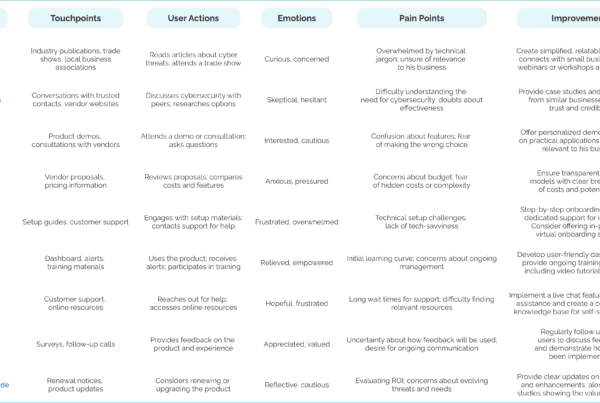
Key insights
I carried out preliminary research with Defendify base users to gain deeper insights into their needs and challenges within the current flow.
“I was completely overwhelmed by the complexity of the cybersecurity solutions available. The technical jargon made it hard to understand what I was actually getting, and I felt lost trying to compare different products.”
- confused Compliance Officer
“The costs associated with cybersecurity platforms are outrageous! I was shocked by the hidden fees and subscription models. It feels like I’m paying a fortune just to keep my business safe.”
- bewildered Business Owner/Entrepreneur
“The amount of training required for my team to effectively use the cybersecurity tools was overwhelming. It took time away from our core work, and I felt like we were losing productivity.”
- overwhelmed Chief Technology Officer (CTO)
U S E R I N S I G H T
User personas
Fictional personas were built using data gathered from user research interviews. Their goals and characteristics represent the needs of a larger group of users. This helped me build empathy, identify patterns of behavior, stress-test designs and humanize user groups.
Problem statement 01
Business Owner
Gene Thompson
Age: 63
Gender: Male
Location: Small town USA
By understanding Gene’s persona, businesses can better tailor their cybersecurity offerings to meet the needs of traditional business owners like him, helping them navigate the complexities of modern technology while safeguarding their legacies.
I N I T I A L D E S I G N
Applying UX Laws
I explored key UX principles for user interface design, using psychological insights to better understand user expectations and enhance the overall experience.
User insight
U S E R I N S I G H T
Usability testing
I carried out a usability study to evaluate the ease with which users could accomplish key tasks within the design. The findings from the study were analyzed, and the insights gained were utilized to refine the designs.
Research type
Location
- US North-East small business
- remote
Participants (7)
- 2 IT Manager/Director
- 1 IT Support Specialist
- 3 Business Owner/Entrepreneur
- 1 Network Administrator
Participants
- 30 minutes session
I N I T I A L D E S I G N
Key insights
K E Y T A K E-A W A Y S
Impact isn't ❌ just about
metrics and numbers
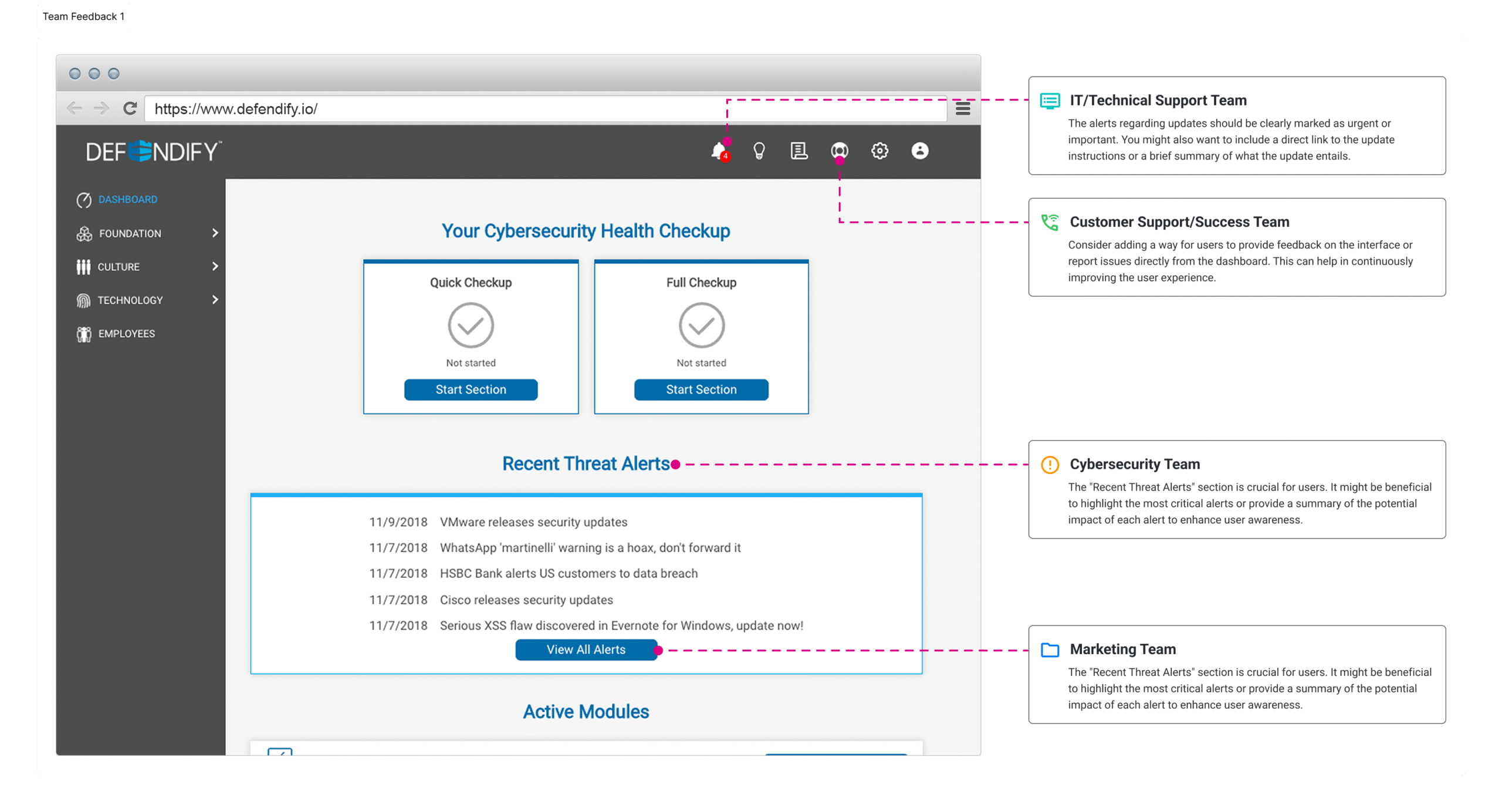
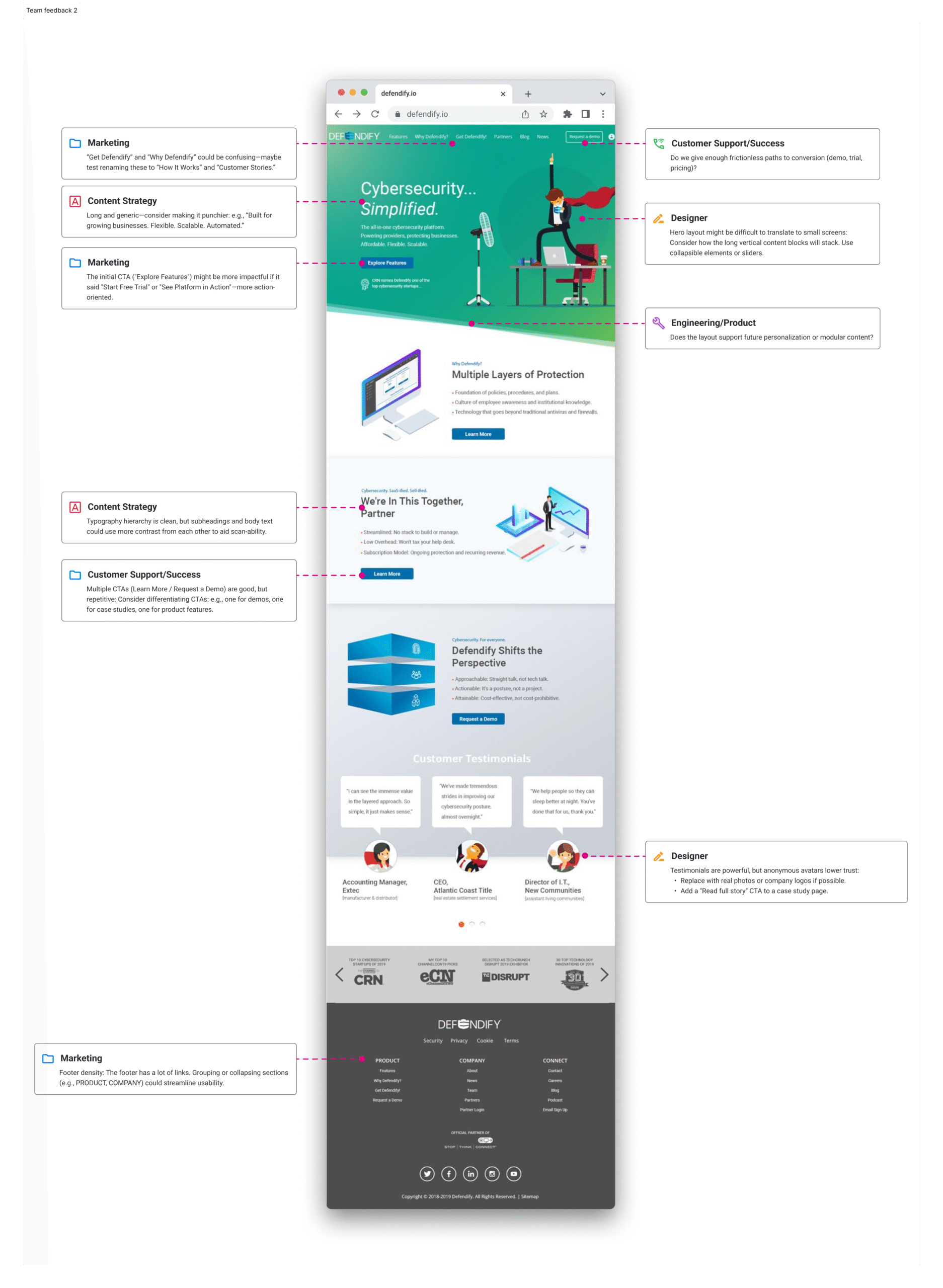
I took sole ownership of designing the end-to-end cybersecurity platform experience for Defendify, focused on making security approachable for small and midsize businesses. Collaborating closely with a cross-functional team, I ensured the solution aligned with user needs, business goals, and technical feasibility, delivering a streamlined product that simplified complex security concepts into clear, actionable steps.
Discovery
-
Simplicity is strategic: The biggest value wasn’t new features, it was removing fear and friction.
-
Language is also UX: Changing a label from “Risk Management Audit” to “Quick Risk Check” drastically improved conversion.
-
Cross-functional collaboration is critical: Working closely with engineering, product marketing, and compliance helped us speak with both user and business.
-
Early feedback saves time: Low-fidelity prototypes caught flow issues that would’ve cost weeks in dev.
Improvements
-
Earlier stakeholder alignment: Clearer alignment between product, compliance, and marketing could have prevented scope shifts and reduced rework during the design-to-dev handoff.
-
More diverse user testing pool: Most usability sessions focused on tech-savvy SMBs; expanding to less digitally fluent users earlier could have uncovered accessibility and comprehension issues sooner.
-
Stronger analytics integration at MVP: Post-launch insights were somewhat limited by the lack of granular usage tracking. Embedding better analytics earlier would have allowed for more data-driven iteration.
-
Scalability considerations in UI: Some layout decisions worked well for the MVP’s 13-tool dashboard, but required rethinking once the platform began scaling with more features and partner integrations.